Add OCSP
SSLUseStapling On SSLStaplingCache "shmcb:/run/httpd/ssl_stapling(32768)"Add HSTS
Header always set Strict-Transport-Security "max-age=63072000;includeSubdomains;"Disable TLSv1.0
SSLProtocol all -SSLv2 -SSLv3 -TLSv1Disabling 3DES ciphers
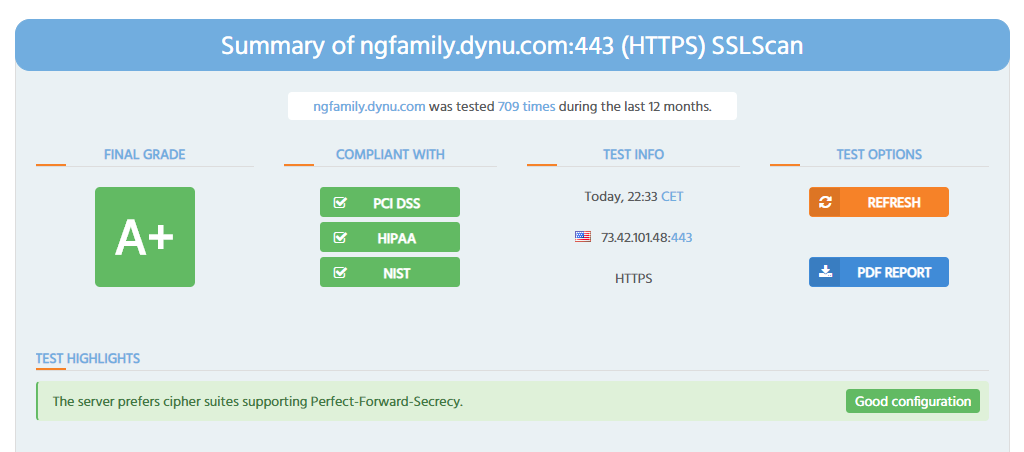
I was working on the ngfamily.dynu.com front end and noticed that the 3des cipher were still accepted:
TLS_ECDHE_RSA_WITH_3DES_EDE_CBC_SHA
TLS_DHE_RSA_WITH_3DES_EDE_CBC_SHA TLS_RSA_WITH_3DES_EDE_CBC_SHAThis fails HIPAA guidance, which I don’t have any information that needs to be protected, but why not disable these ciphers.
Long story short, I found out the problem started from the apache conf from let’sencrypt and so the answer is in /etc/letsencrypt/options-ssl-apache.conf: delete all ciphers with “DES-CBC3-SHA” in the SSLCipherSuite
:ECDHE-ECDSA-DES-CBC3-SHA
:ECDHE-RSA-DES-CBC3-SHA
:EDH-RSA-DES-CBC3-SHA
:DES-CBC3-SHA
SSLCipherSuite ECDHE-ECDSA-CHACHA20-POLY1305:ECDHE-RSA-CHACHA20-POLY1305:ECDHE-ECDSA-AES128-GCM-SHA256:ECDHE-RSA-AES128-GCM-SHA256:ECDHE-ECDSA-AES256-GCM-SHA384:ECDHE-RSA-AES256-GCM-SHA384:DHE-RSA-AES128-GCM-SHA256:DHE-RSA-AES256-GCM-SHA384:ECDHE-ECDSA-AES128-SHA256:ECDHE-RSA-AES128-SHA256:ECDHE-ECDSA-AES128-SHA:ECDHE-RSA-AES256-SHA384:ECDHE-RSA-AES128-SHA:ECDHE-ECDSA-AES256-SHA384:ECDHE-ECDSA-AES256-SHA:ECDHE-RSA-AES256-SHA:DHE-RSA-AES128-SHA256:DHE-RSA-AES128-SHA:DHE-RSA-AES256-SHA256:DHE-RSA-AES256-SHA:AES128-GCM-SHA256:AES256-GCM-SHA384:AES128-SHA256:AES256-SHA256:AES128-SHA:AES256-SHA:!DSS